Retrieving a security Token to make API calls
Introduction
Azure AD B2C
NxtPort International is using Azure Active Directory B2C to provide business-to-customer identity as a service. It uses standards-based authentication protocols including OpenID Connect and OAuth 2.0.
Client Credentials
The OAuth 2.0 Client Credentials flow permits an app (confidential client) to use its own credentials to authenticate when calling web resource, such as REST API. This type of grant is commonly used for M2M (machine-to-machine) interactions that must run in the background, without immediate interaction with a user. Permissions are granted directly to the application itself, by NxtPort International. When the app presents a token to a resource, the resource enforces that the app itself has authorization to perform an action.
The following diagram shows an overview of the components and configuration for a Client Credentials flow.
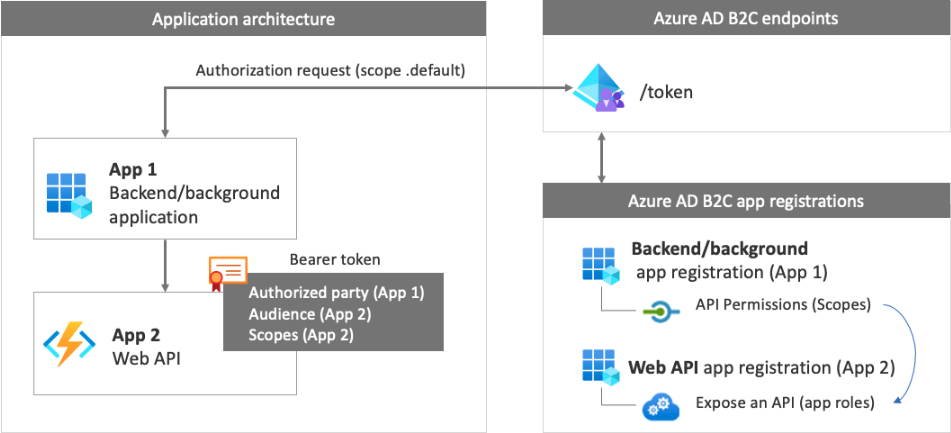
Authentication: Obtain security token
Prerequisites
You have registered on the NxtPort platform
You have received a ClientId & Client Secret from NxtPort
How to retrieve the security token
To generate an authentication request, make an API call towards the Azure AD B2C from NxtPort International. The Tenant ID depends on the environment you want to authenticate against (Live or Staging environment).
ℹ️Please note this information will be provided when you receive the Client ID & secret from the support team.
The POST call has to include the below header and body parameters:
POST https://login.microsoftonline.com/<environment-tenant-id>/oauth2/v2.0/token
Headers:
Content-Type: application/x-www-form-urlencoded
Body:
grant_type: "client_credentials"
client_id: "<your-client-id>"
client_secret: "<your-client-secret>"
scope: "<your-client-id>/.default"This API call, if the provided information is correct, returns the following result:
{
"token_type": "Bearer",
"expires_in": 3599,
"ext_expires_in": 3599,
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtp..."
}The value of the access_token is what you will need to make an authenticated request towards an API hosted by NxtPort International.
In case you receive a 400 or 500 error message and you can't find the source of the problem, please contact the NxtPort support team by creating a support ticket.
Postman sample
Attached to this tutorial, you can find a sample Postman script to connect with the NxtPort platform. You can use them to setup the initial connections.
APIM API Ingestion.postman_collection.json APIM API Ingestion - Stg.postman_environment.json
C# Sample
At NxtPort International, we tend to follow the best practices of Microsoft. Therefore we suggest you use the NuGet package Microsoft.Identity.Web. This is a set of ASP.NET Core libraries that simplifies adding authentication and authorization support to web apps and web APIs integrating with the Microsoft identity platform.
To give you an overview of all needed components, have a look at the following code:
using System.Net.Http.Headers;
using Microsoft.AspNetCore.Authentication.JwtBearer;
using Microsoft.Identity.Client;
var options = new ConfidentialClientApplicationOptions
{
Instance = "https://login.microsoftonline.com",
TenantId = "<environment-tenant-id>",
ClientId = "<your-client-id>",
ClientSecret = "<your-client-secret>"
};
var tokenResponse = await ConfidentialClientApplicationBuilder
.CreateWithApplicationOptions(options)
.Build()
.AcquireTokenForClient(new[] { "<your-client-id>/.default" })
.ExecuteAsync();
using var client = new HttpClient();
client.BaseAddress = new Uri("<api-endpoint-base-address>");
client.DefaultRequestHeaders.Authorization = new AuthenticationHeaderValue(JwtBearerDefaults.AuthenticationScheme, tokenResponse.AccessToken);
using var response = await client.GetAsync("<specific-api-call>");
...When you're using a programming language like .NET, you can also leverage Dependency Injection. The following is a collection of code with the same result as before:
using System.Net.Http.Headers;
using Microsoft.AspNetCore.Authentication.JwtBearer;
using Microsoft.Identity.Client;
var builder = WebApplication.CreateBuilder(args);
...
builder.Services.AddSingleton(_ => ConfidentialClientApplicationBuilder
.CreateWithApplicationOptions(builder.Configuration.GetSection("HttpClients:YourClient:Security").Get<ConfidentialClientApplicationOptions>())
.Build());
builder.Services.AddHttpClient<YourClient>(client => client.BaseAddress = builder.Configuration.GetValue<Uri>("HttpClients:YourClient:BaseUrl"));
var app = builder.Build();
public class YourClient
{
private readonly IConfidentialClientApplication _confidentialClientApplication;
private readonly HttpClient _httpClient;
private readonly IConfiguration _configuration;
public YourClient(IConfidentialClientApplication confidentialClientApplication, HttpClient httpClient, IConfiguration configuration)
{
_confidentialClientApplication = confidentialClientApplication;
_httpClient = httpClient;
_configuration = configuration;
}
public async Task YourMethodAsync()
{
var scopes = _configuration.GetValue<string>("HttpClients:YourClient:Security:Scopes").Split(' ');
var tokenResponse = await _confidentialClientApplication.AcquireTokenForClient(scopes).ExecuteAsync();
_httpClient.DefaultRequestHeaders.Authorization = new AuthenticationHeaderValue(JwtBearerDefaults.AuthenticationScheme, tokenResponse.AccessToken);
using var response = await _httpClient.GetAsync("<specific-api-call>");
...
}
}
appsettings.json:
"HttpClients": {
"YourClient": {
"BaseUrl": "<api-endpoint-base-address>",
"Security": {
"Instance": "https://login.microsoftonline.com",
"TenantId": "<environment-tenant-id>",
"Scopes": "<your-client-id>/.default",
"ClientId": "<your-client-id>",
"ClientSecret": "<your-client-secret>"
}
}
}